While the term “Shadow IT” conjures images of monsters and threats, the reality is less sinister. Shadow IT is any tech used within a company that was not reviewed, approved, and deployed by the company’s IT.
Featured Video: What is Shadow IT? [Explainer]
While the potential is still there for a threat, the reality is that the majority of shadow apps are either harmless or genuinely good for productivity. The problem lies in the lack of visibility that IT has over these unsanctioned tools.
While the default response might be to “shut it down now,” that response puts the IT team in direct conflict with people in the organization. Worse, such an approach often ensures that the IT team will not be consulted about any future technology decisions.
A more measured response can go a long way toward letting IT maintain visibility and administrative capabilities without arresting ownership. If you want that middle group, these steps can help you open dialogue and build trust with your coworkers.
1. Review Security Measures and Protocols
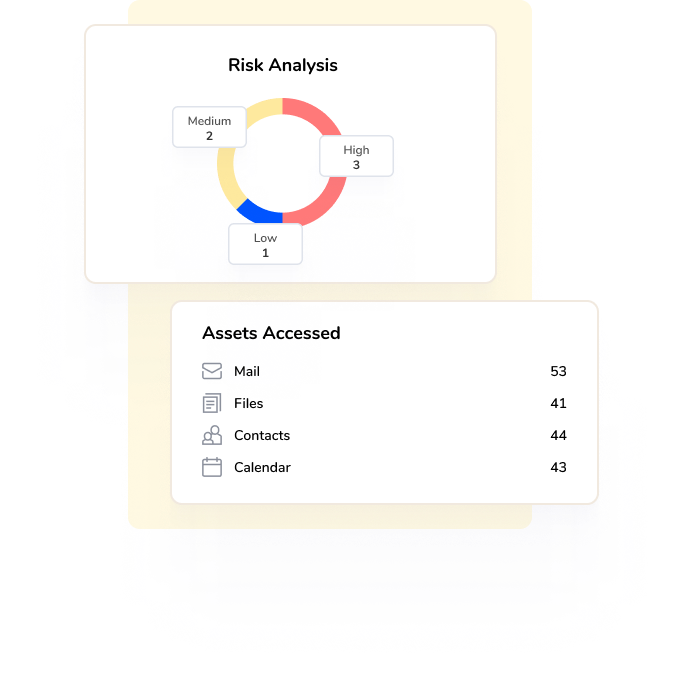
The first thing you should do when you find a shadow app is determine it’s access to sensitive data. If that’s the case, then immediate action may be necessary, especially if personal identification information, payment details, or classified files are at stake.
However, it’s crucial to react proportionately to the identified security risk.
For example, an unauthorized app used for marketing might potentially expose future product plans, but it’s hardly as concerning as an unsanctioned third-party payment system.
Tips for enhancing security:
- Conduct a thorough risk assessment to understand the nature of the threat and potential damage.
- Implement stringent access control policies to limit data exposure.
- Monitor unusual activity or data flow related to the unauthorized app.
- If you have a SaaS Management Platform (SMP) like Torii, check out the app’s security and risk analysis
2. Measuring App Adoption
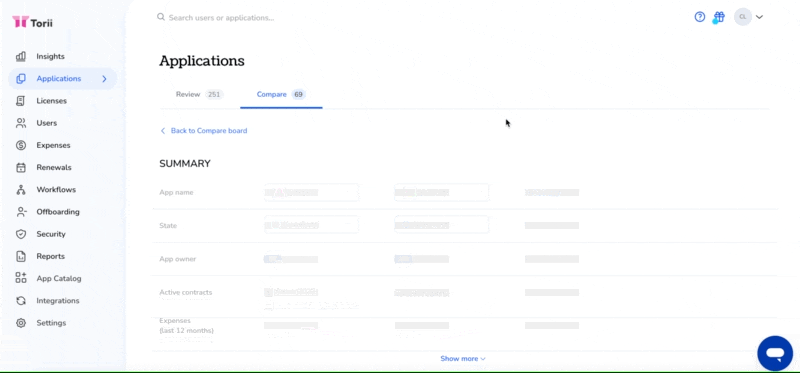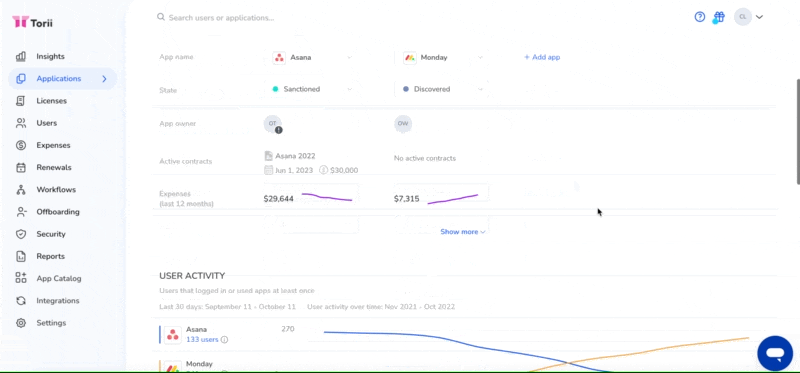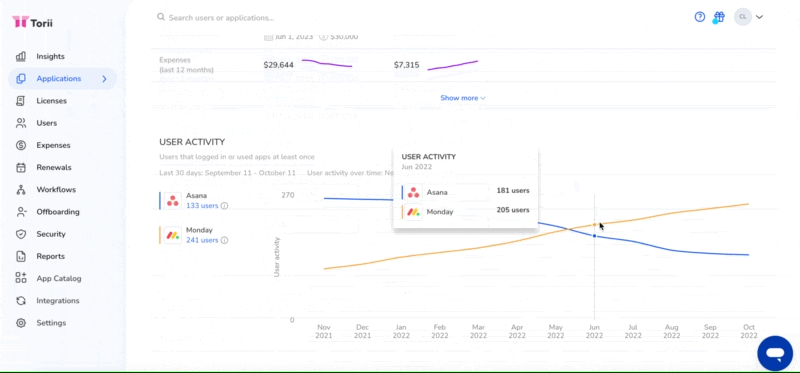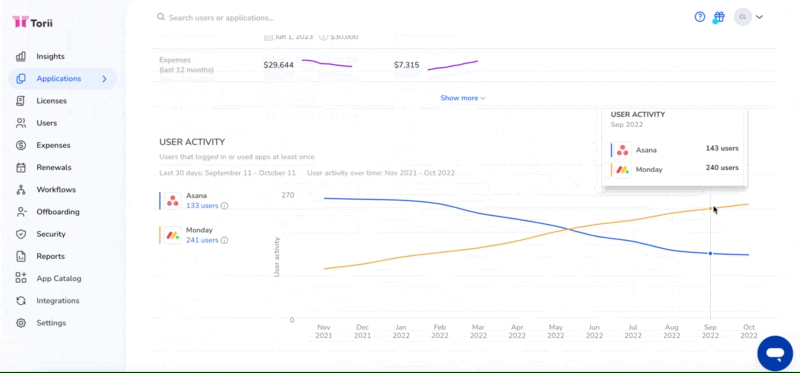
The scale of app adoption within your organization can tell a lot about the underlying issues prompting its usage. Is the app being used by a single employee, a small team, or perhaps even a larger segment of your organization?
Tips for understanding app adoption:
- A small number of people resorting to shadow IT indicates poor communication or awareness about sanctioned apps
- Broad adoption implies a more fundamental issue, such as a lack of trust in the IT team, or a gap in the existing sanctioned SaaS stack.
- Identifying the user base can help to tailor an approach: a focused communication strategy for smaller groups and trust-building measures for larger ones.
- If you have a SaaS Management Platform like Torii, compare usage trends over time and encourage use of the application catalog
3. Identifying Workflow Discrepancies
People often select a tool that optimizes their immediate needs without considering its broader implications. However, locally optimized solutions can lead to complications elsewhere in the organization.
Tips to address workflow concerns:
- Understand the context in which the unauthorized app is being used.
- Identify and mitigate any potential conversion or compatibility issues.
- Facilitate cross-departmental communication to prevent isolated decision-making.
- If you have a SaaS Management Platform like Torii, encourage employees use the application catalog

4. Examining the IT Involvement
When tools are chosen without the guidance of IT, they often lack vital support features, such as reliable backup, support, and business continuity controls. However, not every app necessitates comprehensive IT involvement.
Tips to assess IT involvement:
- Reviewing the features and functions of the discovered app.
- Determining if additional IT measures like backups or support are needed.
- Evaluating the level of technical expertise required by users to effectively use the app.
5. Analyzing Financial Impact
Many organizations inadvertently pay for the same app from multiple budgets. This leads to missing out on economies of scale that vendors often provide for increased usage or quantities. In other cases, employees may purchase alternatives that duplicate an existing corporate subscription.
Tips to find the financial impact:
- Track and consolidate software expenditures across the organization.
- Identify and eliminate redundant software subscriptions.
- Leverage economies of scale by negotiating with vendors for group subscriptions.
- If you have a SaaS Management Platform like Torii, use the expense breakdown to distinguish “shadow expenses” from contracted payments
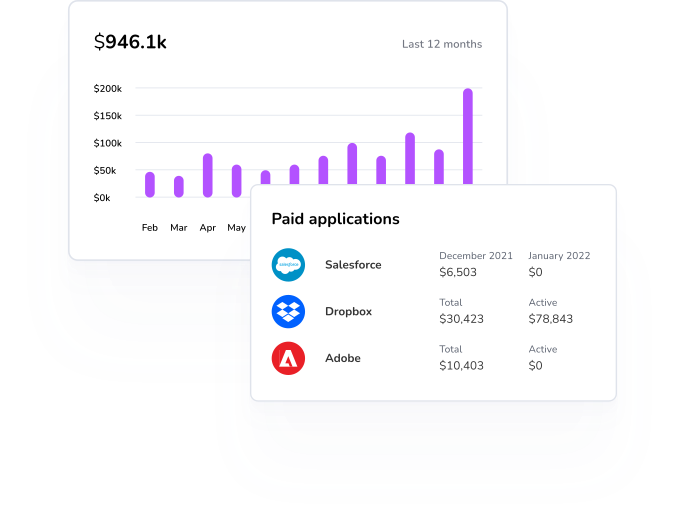
6. Fostering an Environment of Innovation
In many instances, the identification of a new app can be a blessing in disguise. It can indicate innovative ways employees are finding to solve their problems. Apps gain traction not just for their features but also because they align with people’s work habits and preferences.
Tips to embrace innovation:
- Encouraging dialogue with employees to share their preferred tools and practices.
- Continually evaluating and integrating valuable new tools into the corporate tech stack.
- If you have a SaaS Management Platform like Torii, set up automation to collect data about a newly discovered app right away
Devising the Right Response
The worst response to a non-approved app is immediate shutdown or access denial without any dialogue. This approach will foster resentment within your organization. Instead, view the discovery as an opportunity to open a dialogue about why the solution was chosen and the problem it solves.
Creating an environment where your team is the first to be consulted about technological challenges requires building trust, understanding people’s needs, and being patient. Effective IT leadership necessitates active involvement in business operations and processes. When you encounter Shadow IT, you’ve also uncovered an opportunity to start a conversation.

